I’m a big fan of binary reverse engineering. I think it’s a unique skill to have and it creates an interesting way of thinking. The way of thinking that forces you to figure out how things work, even if you’re trying to enjoy some iced tea on the beach. Most of my reversing life has been spent on either x86_64 or ARM64 architectures. I would even go as far as to claim that I know those instruction sets well. However, every now and then I come across a strange looking instruction - like UNPCKLPS, I have to break my flow open the Intel Reference manual and look up the instruction’s meaning. Same for when I’m trying to understand semantics of a very common instruction. For example, SUB can be used atomically if it has the LOCK prefix set - not a detail that comes up often.
A reverse engineer quickly learns to maintain their flow at all costs. Breaking the flow means that the mental representation of the problem breaks down into swiss cheese and makes it ever more difficult to comeback to everything you understood before the break. If you are using IDAPro and you have to break your flow in order to search some PDF document, then that makes life ever more difficult. And so, I built a plugin for IDAPro that removes this problem. It is called IdaRef. What it does is bring the complete instruction set documentation into the IDAPro environment.
Now, IDAPro already provides an auto comments feature. It’s fine, but the feature is a mere translation of the mnemonic into English text. I wanted more. Actually, I got my inspiration from the x86doc which popped up on /r/netsec some time ago. My desire to have full documentation got me thinking: why I can’t I use the same method of parsing the reference manual to integrate it into IDAPro. I wanted not just a re-interpretation, but the original content from the authoritative source.
Releasing IdaRef to the public produced some resonance in the community and several people really liked it. Since that time, I cleaned it up a little more, made it more responsive and even received some nice words from the IDAPro plugin competition (although no prize).
The best part, about releasing to the public, is what the open source community is good at. Several people stepped up and contributed to the plugin and the concept. Chris Czub created a port for Hopper called HopperRef, Sven337 added support for xtensa architecture and Duncan Ogilvie ported it to the x64dbg project. This sort of activity is extremely encouraging for continuing to develop tools that help us do good things. I would like to encourage more people to contribute, particularly more SQL files for supporting more architectures. Generating clean ASCII documentation files is not a trivial task but the result can be used in many different places.
Recently, I developed an open source technique for hooking ARM64 functions on Objective-C applications. It was meant specifically for tracing Objective-C method calls because the technique hooked the objc_msgSend function. There is one piece of the mechanism that was very tricky. It was to modify the branch instructions at runtime to recalculated addresses.
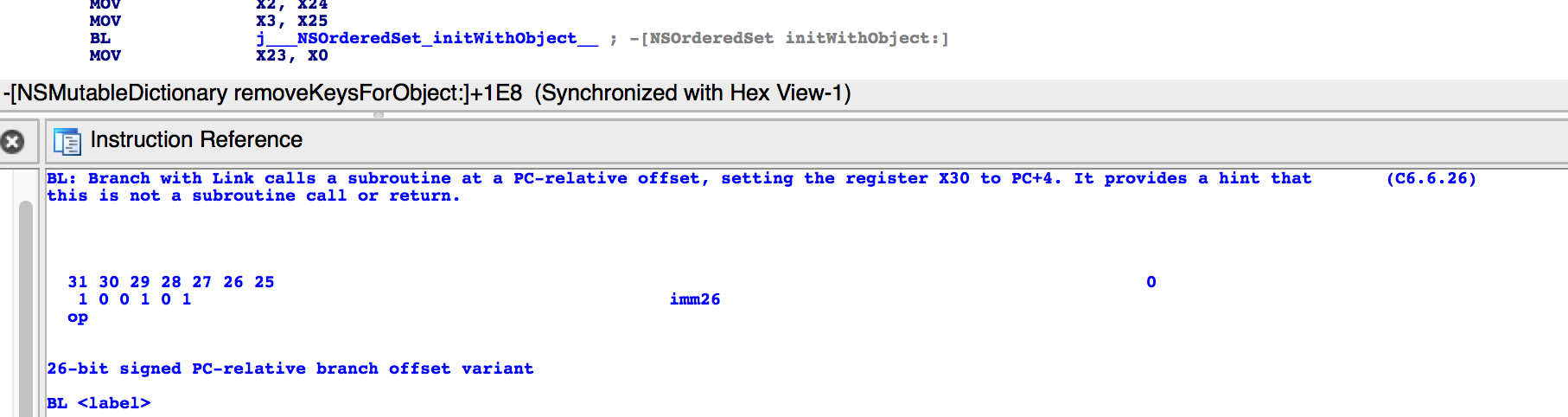
In order to accurately parse and understand the branch instructions, I reversed a few binaries to look at them. I also opened the Objective-C runtime to see the implementation of objc_msgSend function and check exactly which branch instructions were used. It turned out that the PDF to ASCII translation was good enough that I could use the instruction bit placement documentation (as you see in the image above) to write the bit field structs accurately in the hooking implementation.
Enjoy your reversing experience and I hope that IdaRef will help you get more proficient and faster with your art!